Combating Counterfeit Products at the State Level: How to Protect Mobile Devices from Fakes
22 august 2025

The volume of counterfeit goods worldwide continues to grow despite the efforts of governments and businesses to combat the problem. In 2023 alone, customs authorities uncovered 50% more cases of counterfeit products compared to the previous year. Traditional anti-counterfeiting measures such as labeling, holograms, and QR codes are no longer proving effective, while counterfeiters have also learned how to forge mobile device identifiers (IMEI). It’s time for systemic anti-fake solutions—and in this article, we’ll explore exactly what they might be.
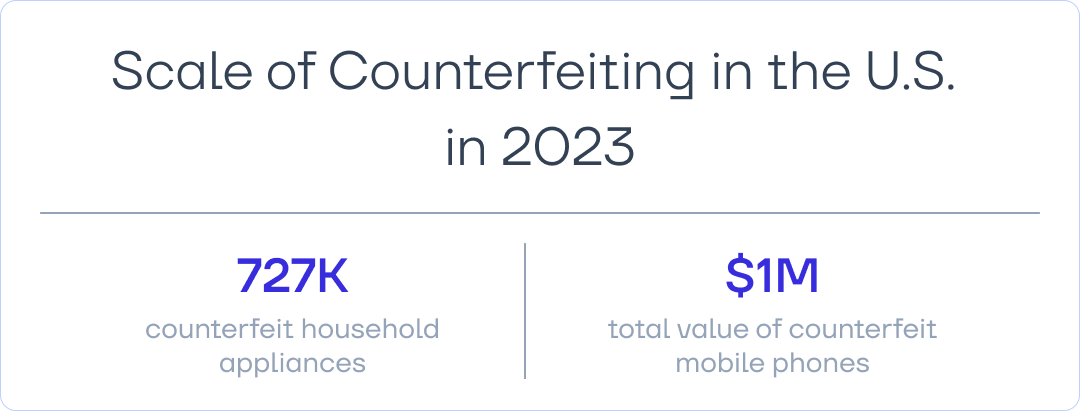
In 2021, counterfeit products accounted for 2.3% of total global trade. In 2023, authorities in the European Union seized 152 million units of illegal products worth over €3.4 billion—a 68% increase compared to 2022. Electronics, including mobile phones, have long been at the top of the most frequently counterfeited goods, alongside clothing, footwear, and leather products.
Source: The Truth Behind Counterfeits (U.S. CBP)
Fraudsters smuggle mobile phones into the country to avoid paying taxes and duties. This has far-reaching consequences for the state as a whole:
Let’s see what measures are currently being used to combat counterfeit products—and why they aren’t working.
Traditionally, manufacturers rely on visual counterfeit protection methods: holograms, QR codes, RFID tags, special packaging, and certificates. But these technologies are no longer effective. The first reason is that counterfeiters replicate these protective elements just as readily—and on the same scale—as the phones themselves.

Source: Mapping Global Trade in Fakes. 2025 Global Trends and Enforcement Challenges (OECD)
The second reason that labeling is ineffective in combating counterfeit goods is that visual protection methods only help distinguish an original from a fake until the device is unboxed. Counterfeit goods can arrive without packaging altogether, rendering such measures useless.
A more reliable tool to prevent counterfeiting is the IMEI (International Mobile Equipment Identity)—a unique 15-digit code assigned to every mobile device during manufacturing. IMEIs help operators block stolen phones, combat “gray” imports, and track the movement of devices. However, even this is not foolproof: counterfeiters have learned to forge IMEIs and bypass control systems.
IMEI Cloning: One number—multiple devices. Fraudsters copy the IMEI from a legitimate device and, using special programming tools, transfer it to other phones. As a result, multiple devices with the same identifier appear on the network. This violates equipment registration requirements and poses risks for subscribers: if one clone is blacklisted (for example, as stolen), all the others with the same IMEI get blocked as well.
IMEI Spoofing: Random numbers instead of legitimate ones. Unlike cloning, spoofing assigns a generated IMEI—either random or non-existent—to the device. This allows the counterfeit to blend in as a legitimate phone and operate on the network until the fraud is detected. Physically, the IMEI on the device is unchanged. Visually, the phone may look authentic, but within the network infrastructure it exists beyond the legal framework.
Changing the IMEI at the hardware level. Counterfeiters tamper with the device’s history, removing records of theft or IMEI swapping—and, most importantly, physically alter the identifier stored in the hardware. This key distinction sets it apart from cloning or spoofing. Tools for changing IMEIs are available on black markets and are widely used in “gray” imports.
Fake IMEI documents and certificates. To create the illusion of legality for counterfeit goods, fraudsters issue forged IMEI registration certificates. At first glance, they look authentic—complete with signatures, stamps, and registration numbers. However, such documents have no legal validity. The buyer ends up with not only an illegal device, but also potential problems when connecting to a network or undergoing verification.
Fraudsters manage to bypass the rules even though IMEI issuance and use are regulated at multiple levels. Current measures fail to protect the rights of copyright holders, manufacturers, and subscribers.
Telecom operators use the GSMA’s global databases to block stolen or illegal phones. Some companies also implement an EIR (Equipment Identity Register) as an anti-fake tool to check IMEIs within their own networks. However, in most countries there is no centralized system that can track and block illegal devices at the national level. Without a coordinated control framework, counterfeit phones can simply move from one operator to another or “resurface” in another coverage area.
For the system to be effective, control must be applied at every stage—from import to network activation. This requires creation of centralized national CEIR (Central Equipment Identity Register) systems, which can unite the efforts of operators, regulators, and customs authorities, ensuring robust protection against counterfeits.
CEIR brings the enforcement of electronics legality into the digital realm, enabling counterfeit phones to be tracked and blocked at the network level.
The CEIR (Central Equipment Identity Register) is a software for the centralized registration of mobile devices by their IMEI codes. It collects information from telecom operators via EIR and from customs authorities, providing a single reliable source of data on all devices in the country.
CEIR maintains a database of phones but does not interact with them directly. For example, a national regulator can import the GSMA blacklist into CEIR, which will then distribute it to all mobile operators in the country. If an operator’s EIR detects an IMEI from the blacklist, the device will be blocked from accessing the mobile network.
In the fight against counterfeit products, CEIR makes it possible to: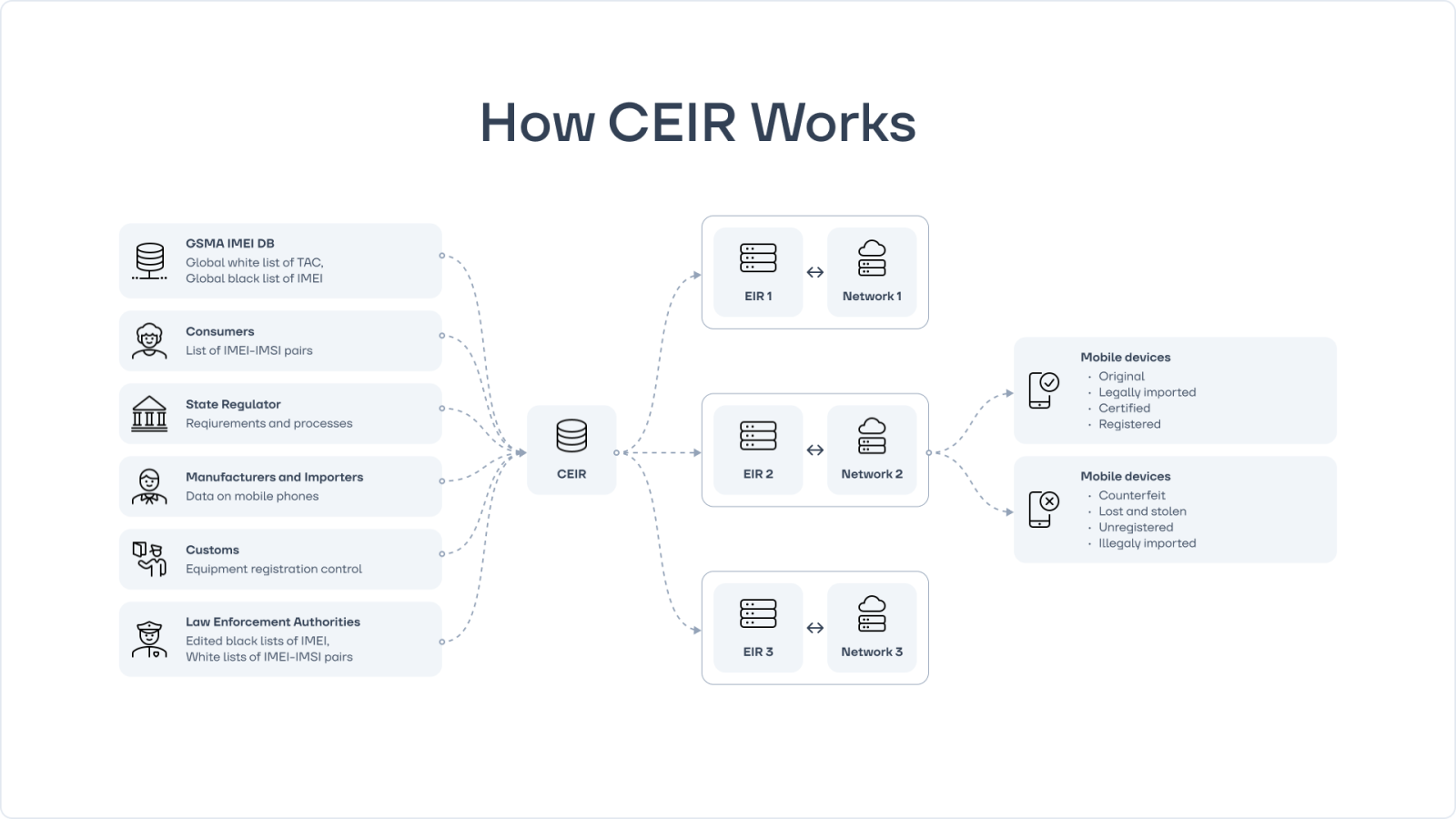
CEIR consolidates data from EIR systems, customs authorities, manufacturers, and subscribers, creating a complete and accurate picture of the mobile phone market
EW CEIR Integration Scenarios
CEIR is a modern tool for increasing market transparency. It helps combat the spread of illegal products, protecting the interests of the government, businesses, and consumers, while boosting national budget revenues. Implementing a centralized device registration system can be the solution to the problem of counterfeit mobile phones in the country.
More News
Global Losses from Counterfeit Goods
In 2021, counterfeit products accounted for 2.3% of total global trade. In 2023, authorities in the European Union seized 152 million units of illegal products worth over €3.4 billion—a 68% increase compared to 2022. Electronics, including mobile phones, have long been at the top of the most frequently counterfeited goods, alongside clothing, footwear, and leather products.

Source: The Truth Behind Counterfeits (U.S. CBP)
Fraudsters smuggle mobile phones into the country to avoid paying taxes and duties. This has far-reaching consequences for the state as a whole:
- deprives the national budget of a portion of its revenue
- fuels the illegal trade in mobile devices
- facilitates the spread of malicious apps that compromise subscribers’ personal data
- undermines trust in legitimate retailers and telecom operators
Let’s see what measures are currently being used to combat counterfeit products—and why they aren’t working.
Why Anti-Fake Tools don’t Work—Even with IMEI
Traditionally, manufacturers rely on visual counterfeit protection methods: holograms, QR codes, RFID tags, special packaging, and certificates. But these technologies are no longer effective. The first reason is that counterfeiters replicate these protective elements just as readily—and on the same scale—as the phones themselves.

Source: Mapping Global Trade in Fakes. 2025 Global Trends and Enforcement Challenges (OECD)
The second reason that labeling is ineffective in combating counterfeit goods is that visual protection methods only help distinguish an original from a fake until the device is unboxed. Counterfeit goods can arrive without packaging altogether, rendering such measures useless.
A more reliable tool to prevent counterfeiting is the IMEI (International Mobile Equipment Identity)—a unique 15-digit code assigned to every mobile device during manufacturing. IMEIs help operators block stolen phones, combat “gray” imports, and track the movement of devices. However, even this is not foolproof: counterfeiters have learned to forge IMEIs and bypass control systems.
How Counterfeiters Fake IMEIs
Typically, criminals use one of the four main schemes.IMEI Cloning: One number—multiple devices. Fraudsters copy the IMEI from a legitimate device and, using special programming tools, transfer it to other phones. As a result, multiple devices with the same identifier appear on the network. This violates equipment registration requirements and poses risks for subscribers: if one clone is blacklisted (for example, as stolen), all the others with the same IMEI get blocked as well.
IMEI Spoofing: Random numbers instead of legitimate ones. Unlike cloning, spoofing assigns a generated IMEI—either random or non-existent—to the device. This allows the counterfeit to blend in as a legitimate phone and operate on the network until the fraud is detected. Physically, the IMEI on the device is unchanged. Visually, the phone may look authentic, but within the network infrastructure it exists beyond the legal framework.
Changing the IMEI at the hardware level. Counterfeiters tamper with the device’s history, removing records of theft or IMEI swapping—and, most importantly, physically alter the identifier stored in the hardware. This key distinction sets it apart from cloning or spoofing. Tools for changing IMEIs are available on black markets and are widely used in “gray” imports.
Fake IMEI documents and certificates. To create the illusion of legality for counterfeit goods, fraudsters issue forged IMEI registration certificates. At first glance, they look authentic—complete with signatures, stamps, and registration numbers. However, such documents have no legal validity. The buyer ends up with not only an illegal device, but also potential problems when connecting to a network or undergoing verification.
Fraudsters manage to bypass the rules even though IMEI issuance and use are regulated at multiple levels. Current measures fail to protect the rights of copyright holders, manufacturers, and subscribers.
How IMEIs are Monitored—and Why That’s Not Enough to Combat Counterfeit Goods
The GSMA—the Global System for Mobile Communications Association—maintains several key registries:- TAC List (Type Allocation Code)—an 8-digit identifier assigned to manufacturers to designate specific device models. These codes form the first part of the IMEI and are combined with a unique serial number of the SIM module to create the full identifier.
- IMEI Blacklist—used to block stolen or lost phones. Telecom operators add devices to the list when subscribers report them and can then submit these records to the GSMA. This forms a unified global database. Once blacklisted, a mobile phone can no longer connect to communication networks.
Telecom operators use the GSMA’s global databases to block stolen or illegal phones. Some companies also implement an EIR (Equipment Identity Register) as an anti-fake tool to check IMEIs within their own networks. However, in most countries there is no centralized system that can track and block illegal devices at the national level. Without a coordinated control framework, counterfeit phones can simply move from one operator to another or “resurface” in another coverage area.
For the system to be effective, control must be applied at every stage—from import to network activation. This requires creation of centralized national CEIR (Central Equipment Identity Register) systems, which can unite the efforts of operators, regulators, and customs authorities, ensuring robust protection against counterfeits.
CEIR—A Centralized Solution for Mobile Device Control
CEIR brings the enforcement of electronics legality into the digital realm, enabling counterfeit phones to be tracked and blocked at the network level.
The CEIR (Central Equipment Identity Register) is a software for the centralized registration of mobile devices by their IMEI codes. It collects information from telecom operators via EIR and from customs authorities, providing a single reliable source of data on all devices in the country.
CEIR maintains a database of phones but does not interact with them directly. For example, a national regulator can import the GSMA blacklist into CEIR, which will then distribute it to all mobile operators in the country. If an operator’s EIR detects an IMEI from the blacklist, the device will be blocked from accessing the mobile network.
In the fight against counterfeit products, CEIR makes it possible to:
- determine whether a device is officially registered
- detect cloned IMEIs and manage dispute resolution
- automatically block counterfeit devices before they are activated on the network

CEIR consolidates data from EIR systems, customs authorities, manufacturers, and subscribers, creating a complete and accurate picture of the mobile phone market
EW CEIR Integration Scenarios
| Who It Interacts with | How | What It Delivers |
| Telcos | A mobile operator sends CEIR data on all devices in its network (IMEI, IMSI) and receives from CEIR IMEI and IMEI–IMSI lists (black, white, and gray). Based on these lists, the operator decides whether a number should be blocked. |
– Prevents counterfeit or “gray market” devices from connecting to the network. – Helps ensure services are provided only to subscribers with registered devices, reducing the risk of fraud. |
| Customs authorities | Receives data on officially imported devices, including IMEI lists from importers. Verifies payment of duties and fees. | Reduces illegal imports: bringing in unregistered devices becomes pointless, as any detected violations lead to those devices being blocked—making them unsellable. |
| Ministry of Finance | Transfers data on officially imported and manufactured devices and automatically applies fiscal mechanisms for device registration. | Enables tax revenue forecasting and increases contributions to the national budget, including through paid services for registration, analytics, and API access for companies and manufacturers. |
CEIR is a modern tool for increasing market transparency. It helps combat the spread of illegal products, protecting the interests of the government, businesses, and consumers, while boosting national budget revenues. Implementing a centralized device registration system can be the solution to the problem of counterfeit mobile phones in the country.
Learn more about EW CEIREW CEIR is Eastwind’s solution for registering and controlling user equipment in mobile networks.
Key features of EW CEIR:
- Registration and deregistration of mobile phones
- Distribution of IMEI blacklists and whitelists, as well as IMSI–IMEI lists, to mobile operators
- Tracking counterfeit, smuggled, and stolen devices
- Linking a device to a specific person (personal ID)
- Identifying subscribers using a particular phone
- Verifying devices before sale or purchase
