How Telecom Operators Monetize A2P Traffic with SMS Firewalls
How Fraudsters Bypass A2P SMS Delivery Rules
Dishonest SMS aggregators and content providers use a variety of tactics to send A2P messages at the lower P2P rates:
- Number Spoofing. To cut costs on international traffic, aggregators replace international Sender IDs with local ones and route messages through domestic operators or SMS aggregators. This allows them to deliver A2P SMS at a fraction of the standard cost.
- Routing SMS Through Intermediaries. Operators pay each other a fixed fee for message delivery. Fraudulent aggregators exploit this by lengthening the delivery chain. They send international A2P messages to partners with lower rates, who then pass them on to the final operator at a flat cost—without paying per message—thus avoiding standard A2P charges.
- Using P2A Messages. Some services design their messaging flows so that the subscriber initiates SMS—for example, by sending a code to an app for verification. In the system, this is classified as an MO (Mobile Originated) message, which is billed at the user’s rate rather than the more expensive A2P tariff. This significantly reduces termination costs for the service provider.
- Using SIM Boxes. This remains the most widespread method of bypassing legitimate routes. Fraudsters use devices loaded with dozens or even hundreds of SIM cards to send commercial A2P messages at lower P2P rates.
.png)
Source: Global A2P SMSreport. The complete overview 2017–2027 (Mobilesquared)
These three schemes generate around $8 billion a year for fraudsters. SMS Firewalls can help mobile operators prevent these financial losses.
Monetization Strategies for A2P Traffic Used by Operators
Operators can boost A2P traffic revenue without significant infrastructure investment by adopting a well-thought-out monetization model and building a strong partner ecosystem. The key is to choose the right pricing strategy and establish transparent relationships with aggregators and service providers. A crucial element of any strategy is the SMS Firewall, which serves as a traffic control tool and helps achieve revenue targets.
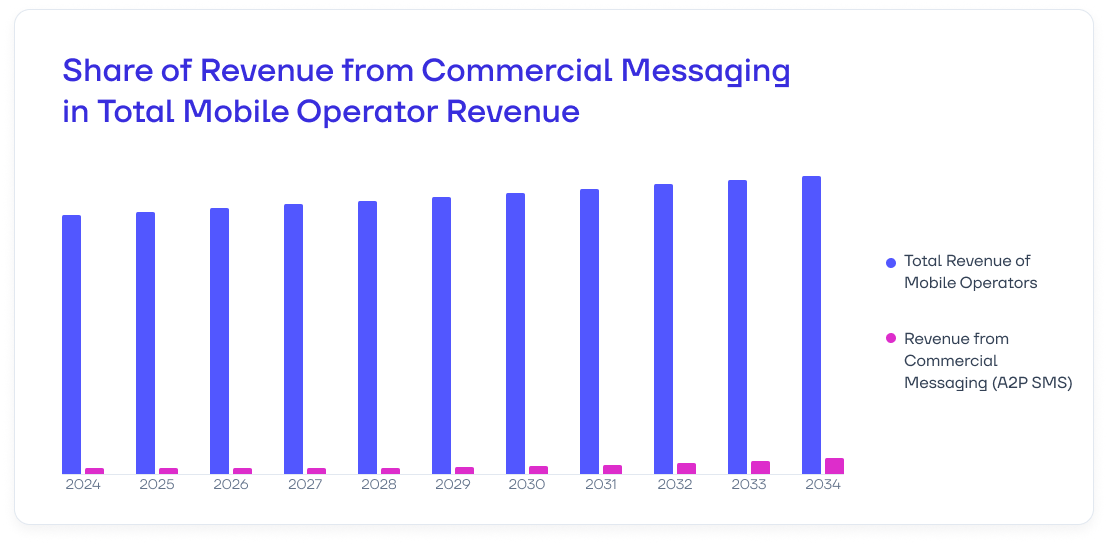
The share of revenue from commercial SMS delivery in mobile operators’ total income is steadily growing and is projected to reach 3.44% by 2034
Source: CAN MOBILE OPERATORS STILL MAKE MONEY FROM MESSAGING 3 YEARS FROM NOW? (Mobilesquared)
How Mobile Operators Monetize A2P Traffic Using SMS Firewalls:
Signing Direct Contracts with Major Senders. Some SMS aggregators disguise A2P traffic from large services to cut costs, but SMS Firewalls detect and block these "gray-route" messages. As a result, senders—such as banks, retailers, or delivery services—see their messages failing to reach customers and often decide to switch providers. They tend to favor partners who can guarantee reliable delivery, even at a higher rate. For operators, this opens the door to securing direct contracts and earning more through transparent traffic termination.
Revenue Sharing with Aggregators. In this model, an operator routes its SMS traffic through an aggregator and receives a percentage of the revenue from commercial message delivery. This allows the aggregator to earn income without investing in infrastructure or acquiring B2B clients, while the operator monetizes A2P traffic with minimal effort. An SMS Firewall enables the aggregator to eliminate dishonest partners using "gray routes", ensuring clean traffic for the operator and delivering the expected additional revenue.
Building a Dedicated SMS Hub. This approach requires significant investment, but it gives the operator full control over the routing and monetization of A2P traffic. In this scenario, the operator acts as a regional hub, handling traffic for other operators. This opens new revenue streams and strengthens its market position. To make the investment pay off and ensure profitability, the operator must secure its network against "gray-route" SMS.
Partnership Terms and Quality Metrics. Partnership agreements between mobile operators and aggregators should include clear quality metrics—such as traffic volume, delivery rate and speed, and transparency of reporting. In the next section, we’ll explore how SMS Firewalls support these objectives.
How an SMS Firewall Helps Monetize A2P Traffic
An SMS Firewall is a platform that analyzes and filters SMS traffic in real time. Its anti-fraud capabilities allow operators not only to protect their networks but also to generate revenue from international A2P messages.
How an SMS Firewall Works
An SMS Firewall is integrated between the mobile operator’s SMS center and external traffic sources, creating a single control point for all inbound and outbound messages.The anti-fraud solution connects to the SMS center using standard protocols, without requiring changes to the operator’s existing infrastructure:
- SMPP (Short Message Peer-to-Peer Protocol)
- MAP over SS7 (Signaling System No. 7)
- Diameter (for 4G/LTE networks)
If needed, the system can also be adapted to work with other platforms, such as Apache Kafka.
The SMS Firewall gives mobile operators and aggregators the ability to monitor and control all message traffic. Its features help telecom companies tackle key market challenges: uncovering fraudulent schemes, blocking suspicious activity, and boosting revenue. These capabilities can be grouped into two categories—basic and advanced, with the latter enhanced by artificial intelligence.
Case Study: Mobile Operator Zain Kuwait Sees the EW SMS Firewall as a Revenue-Generating Asset
Within just three months of deploying the EW SMS Firewall, over 6.7 million "gray-route" A2P SMS messages were detected. The operator’s estimated lost revenue from this unauthorized traffic was $188,000. Since then, Zain Kuwait has eliminated these losses and successfully monetized its international A2P traffic.
How We Helped the Operator Boost Revenue with the EW SMS Firewall
Core SMS Firewall Capabilities for Monetization
Traditionally, an SMS Firewall is designed to protect against fraud, block spam, and provide analytics to help control and monetize traffic. Let’s take a closer look at these core functions:
Detection of A2P SMS in Traffic Streams. The firewall distinguishes commercial (A2P) traffic from person-to-person (P2P) messages using algorithms that analyze a wide range of parameters:
- By traffic source: The system checks the origin of both P2P and A2P messages. It verifies identifiers like IMSI and MSISDN for subscriber messages, and alphanumeric Sender IDs or short codes for commercial ones. If inconsistencies are found—such as a local MSISDN paired with an international Global Title—the system flags the message as fraudulent.
- By content: The firewall scans message texts for repeated patterns, templates, shortcodes, and specific symbols. For example, if a message from a subscriber number contains a verification code from an OTT service, the system identifies it as fraudulent.
.png)
Fraudsters disguise international A2P traffic as P2P, depriving mobile operators of revenue
Depending on the configuration, the system can either immediately block the sender or flag the message for further analysis by the vendor’s specialists.
Real-Time Monitoring. An SMS Firewall continuously monitors the operator’s entire message traffic and can respond even without predefined rules. For instance, the system can detect the onset of an SMS attack and instantly block the sender’s number.
System performance analytics are displayed on dashboards and in reports. They show the volume of local and international messages, revenue, blocked threats, and statistics on aggregator partners. The mobile operator uses this data to claim compensation from a counterparty or to remove them from the SMS delivery chain altogether if they repeatedly violate the rules.
.png)
The EW SMS Firewall dashboard gives operators a clear view of the volume of A2P traffic flowing through their network—both from individual partners and overall
The core capabilities of an SMS Firewall can be enhanced with artificial intelligence. For example, EW SMS Firewall includes an AI module that improves the accuracy of fraud detection, reduces the workload on staff, and offers additional advantages for real-time operations.
Capabilities of an AI-Enhanced SMS Firewall
The AI & ML module integrated into an SMS Firewall automatically analyzes SMS traffic to detect A2P fraud and the use of SIM boxes within the operator’s network.The EW SMS Firewall’s AI module operates in two modes:
- Real-time mode—for immediate detection and response
- Post-analysis mode—for asynchronous processing
In real-time mode, the system quickly identifies "gray-route" traffic, blocks it instantly, updates filtering rules on the fly, and applies them immediately. In post-analysis mode, the system does not block fraudulent messages but flags them and collects statistics for further tuning by specialists. Aside from the blocking functionality, both modes offer the same detection and analysis capabilities.
Content Analysis. The AI module analyzes SMS content to detect hidden authorization codes and other sensitive data. It uses natural language processing (NLP) models and multilingual message analysis to do so. The system employs Named Entity Recognition (NER) to classify messages based on fraud indicators. These algorithms effectively identify suspicious patterns—even when obfuscated—allowing operators to respond swiftly to potential threats.
Tariff-Based Segmentation. The AI classifier within the anti-fraud module segments A2P traffic by message type—such as banking alerts, service notifications, or marketing campaigns. Operators can assign different rates to each category, enabling more flexible and targeted revenue management.
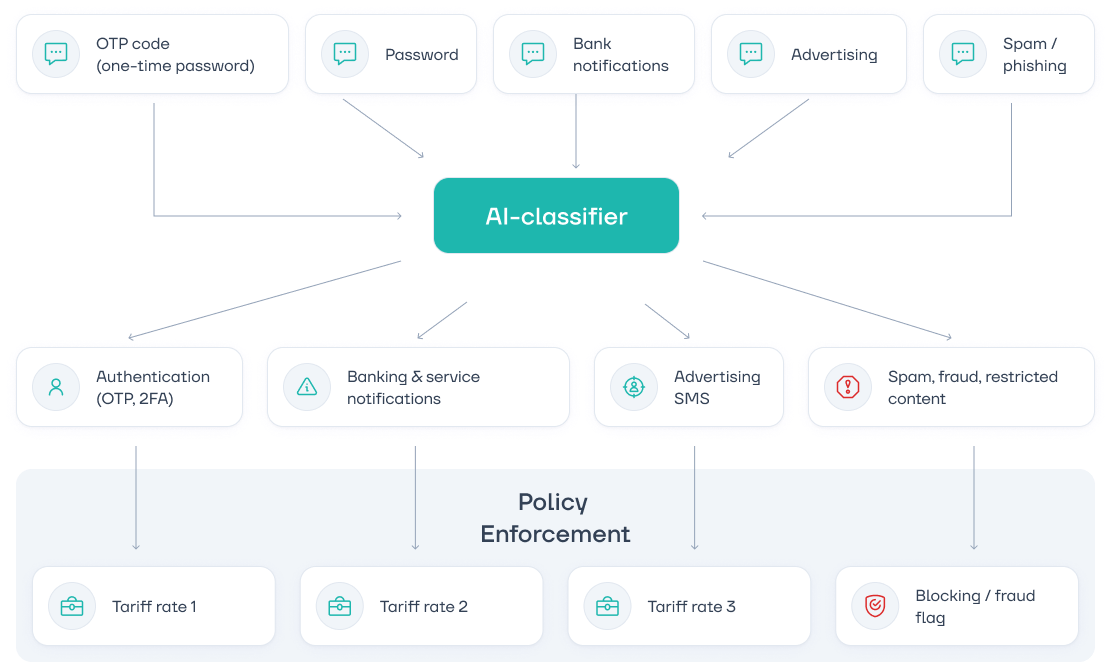
The AI module of EW SMS Firewall classifies messages and automatically applies different tariffs based on their type, while spam and fraudulent messages are either blocked or flagged for review
Automated Rule Enforcement. The EW SMS Firewall allows operators to configure rules for the AI module’s behavior. For example, the system can be set to automatically block messages flagged as "fraud" based on its analysis. This significantly enhances the efficiency of the solution while reducing the workload on specialists.
EW SMS Firewall gives operators a clear and transparent view of A2P traffic—from message types to sources of fraud. This data serves as a foundation for:
- Optimizing routing and eliminating unauthorized channels
- Developing a well-grounded and strategic pricing policy
- Increasing revenue from international traffic termination
Let’s take a look at the strategies telecom operators use to increase revenue from international A2P traffic termination.
What It Takes to Implement an SMS Firewall
Installing an SMS Firewall typically takes 3 to 4 months and involves both technical and organizational preparation. Let’s look at what mobile operators need to consider to successfully monetize A2P traffic.
"When an SMS aggregator approaches us to implement the EW SMS Firewall, we start by assessing the economic viability: we analyze the market and calculate the potential revenue the client can generate by protecting their traffic.
Next, we move on to a technical assessment: we examine the network architecture, the protocols in use, infrastructure requirements, and the expected load.
Based on this data, we prepare the project documentation—both the High-Level Design and the Low-Level Design. If the architecture requires customization (for example, Apache Kafka), we simultaneously make the necessary adjustments to the product.
Together with the operator, we assemble an implementation team, assign roles, and define areas of responsibility for each stage of the project. This ensures transparency and control throughout the process."
— Andrey Alematsev,
Product Manager, the EW SMS Firewall
Technical Requirements
To launch an SMS Firewall, the operator needs a basic telecom infrastructure and access to key A2P message routing points. Typically, the following is sufficient:
- Connection to SMSC / SS7 / Diameter / HTTP API—depending on the network architecture
- A dedicated local or virtual server with specified performance parameters
Exact technical specifications will vary based on the operator’s traffic volume and infrastructure specifics.
Case Study: Implementing the EW SMS Firewall in a Network with a Non-Standard Architecture
We helped an aggregator increase revenue from international A2P traffic termination by integrating the anti-fraud solution with Apache Kafka. To support the deployment, the client purchased three servers along with other hardware. Our team reworked the SMS processing logic to boost message handling speed—from 10–20 seconds down to just 1 second for incoming messages.
Initially, the client planned to handle 40,000 A2P SMS per day. However, just nine months after integrating the EW SMS Firewall, they exceeded their KPI by 33%, processing 60,000 messages daily—which resulted in significantly increased revenue.
How SMS Aggregator Secured Its Network from “Gray-Route” A2P Traffic with the EW SMS Firewall
Specialist Teams
Implementing an SMS Firewall requires collaboration between the vendor’s team and the customer’s team. For example, the EW SMS Firewall integration project with Apache Kafka involved a total of 20 specialists.
- The customer’s team provides network access, sets up gateways and routing, and manages integration with monitoring systems
- The vendor’s team configures traffic filtering rules, reporting tools, blacklists, and whitelists
Once integration is complete, the SMS Firewall undergoes a two-stage testing process:
- Load testing confirms the system’s ability to handle peak traffic volumes
- Functional testing verifies the accuracy of message filtering
These testing phases typically take about a week, assuming no complications.
An SMS Firewall is a vital component for telecom operators aiming to protect their networks and monetize international A2P traffic. Eastwind’s solution meets these needs—helping operators not only block fraud but also build a transparent, revenue-driven model tailored to their specific infrastructure.
Learn more about the capabilities of the EW SMS Firewall
